It’s easy to think your small business doesn’t need cybersecurity solutions. After all, who cares about your small amount of data?
You’d be surprised.
Think about it this way. If you wanted to steal a car, would you go for the one with top security or the older model that’s straightforward to break into?
Small businesses are the most frequent targets for cybersecurity attacks because it’s easier for hackers to breach these systems.
Big enterprises often have watertight security systems, whereas small business owners tend to overlook their importance.
But while it might be super important, it can be confusing to understand where to start with small business security.
Let’s dive into the different types of cybersecurity solutions and how they keep small businesses safe from hacks and breaches.

Why are Cybersecurity Solutions so Important for Small Businesses?
For small-to-medium businesses (SMBs), cybersecurity is paramount. But most small business owners don’t realize this, leaving them vulnerable to attacks.
You wouldn’t leave your shop unlocked overnight, so why leave your online assets open to thieves and malicious actors?
But as Menny Barzilay, Cytactic cofounder, explains …
“Many small business owners think that their business is not interesting enough for hackers to notice or that they don’t hold any valuable assets that hackers would like to compromise. Which is obviously wrong.”
In fact, a staggering 73% of small businesses had trouble with hackers or data leaks last year.
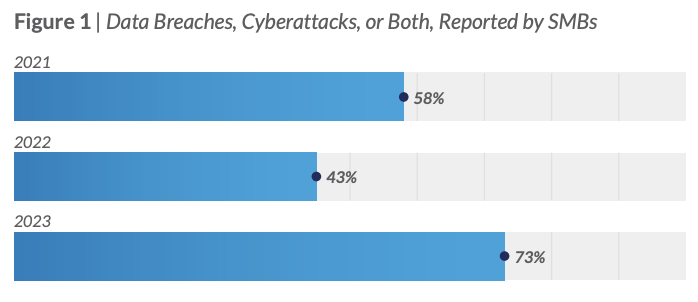
This might seem surprising at first, but it makes sense. Hackers find it easier to infiltrate small businesses than large enterprises. For example, SMBs experience 350% more social engineering attacks than big businesses do.
And the impact is disastrous.
When hackers get in, it costs a lot of money to fix your systems and get your business back up and running.
Almost 40% of small businesses who got hacked last year said it cost them over $250,000.
And it’s not just about the direct costs.
According to the Harvard Business Review, cyberattacks will sink your stock prices, with the costs being felt across the whole business ecosystem. Not only that, but it also affects your company’s credit rating, leading to higher borrowing rates.
On top of the financial ramifications, you’ll have recovery time to worry about. You’ll need time to restore your systems.
This affects business continuity as you won’t be able to operate until you know everything is safe.
Perhaps the most damaging thing is the effect on your reputation.
When a company experiences a cyberattack or data breach, it signals to customers that they can’t trust you to protect their information. A loss of trust can mean loyal customers switch to a competitor, while new customers simply choose a different provider from the get-go.
The problem is that cybersecurity risks are as dynamic as they are dangerous.
With constantly evolving threats, you need a multi-pronged security system to protect you from all angles.
Let’s explore the kinds of solutions including new 2024 tools an SMB would need.
Top 13 Cybersecurity Solutions for Small Businesses
For SMBs, comprehensive cybersecurity solutions are key to safeguarding against the broad spectrum of cyber threats. For total coverage, your solutions should offer all-around protection, complete visibility, and actionable insights.
This helps you combat the potential threats you know about while protecting you against the unknown threats you’re unaware of.
1. Antidetect Browser
Many cyber attack types, like malware threats and phishing scams, rely on gathering information about your online behavior and habits. To protect yourself against these threats, you need a way to mask these behaviors.
An antidetect browser camouflages and protects your online identity. It hides your digital fingerprint, so your browsing activities are untraceable.
For SMBs, this acts as a layer of online anonymity that makes it nearly impossible for hackers to target your real digital identity.
For businesses that need anonymous surfing to protect their digital fingerprint, GoLogin offers a reliable antidetect browser solution. It will provide completely anonymous browsing that’s also helpful for marketing needs such as running multiple accounts with no restrictions.
Originally privacy tools, antidetect browsers like GoLogin are mainly used by marketers to run multiple accounts on social media without restrictions.
Named Easiest to use Antidetect browser according to G2, GoLogin is an essential tool for comprehensive protection against identity-based cyber attacks and account loss.
2. Antivirus Software
41% of SMBs have installed antivirus or malware protection as cybersecurity solutions in the last year.
These are the first line of defense against some of the most infectious and dangerous threats that steal data and lock you out of your systems. Antivirus software acts like a guard dog for your devices. It keeps a look out for signs of viruses and malware before they breach your system.
With the right antivirus software, you’re protected against viruses, worms, trojans, spyware, phishing attacks, and ransomware.
3. Domain Name System (DNS) Protection
DNS protection acts like a smart filter for your internet connection. It stops employees from inadvertently visiting phishing sites and online scams.
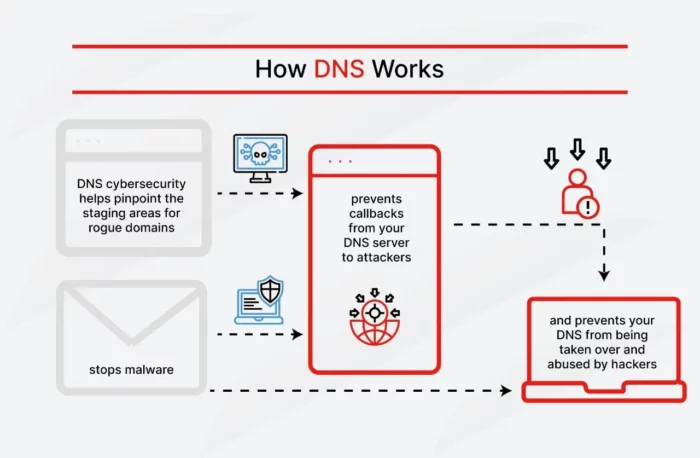
DNS attacks might reroute you to a malicious website, exploit your DNS vulnerabilities, or overwhelm your servers. Attackers do this to steal sensitive data, disrupt business security operations, and spread malware.
Without DNS protection, it’s far easier for hackers to trick your employees into revealing personal data or clicking on a dangerous link.
4. Threat Detection
Threat detection and response systems watch over your online activities, looking out for signs of cyber threats.
They’re not looking for intruders who are already trying to breach the system. Threat detection actively seeks out potential risks before they can do harm.
These types of cybersecurity tools spot threats like malware, ransomware, and phishing scams early.
Without threat detection, your business won’t notice these threats until it’s too late. Instead of threats, they escalate to real problems with stolen data, locked files — or worse.
If you don’t have threat detection, a breach will feel like finding a hole in your boat when you’re already sinking.
5. Intrusion Detection and Prevention (IDS/IPS)
Intrusion detection systems protect you against attacks that make it to your network. These systems offer real-time monitoring of your online traffic, spotting hackers before they break in.
IDS and IPS work in unison to protect against unauthorized network access control and attacks on or within your system that you might not even notice without the software.
Together, they act like the watchman and the bodyguard.
IDS monitors network traffic for suspicious activity, while IPS takes steps to prevent threats from entering your network.
Without IDS/IPS, it’s easier for hackers to sneak in, steal sensitive information, or take over your systems.
6. Next-Generation Firewalls (NGFW)
Next-generation firewalls inspect the content of the internet traffic that enters and exits your business. These high-powered firewalls block sophisticated cyberattacks in ways that older firewalls can’t.
With these systems, you’re better protected against things like advanced malware and application-layer attacks. Without NGFWs, you’re vulnerable to complex attacks that sneak past basic security.
While security systems might have improved, cyber threats constantly evolve, and hackers get wiser.
NGFWs act like an increasingly stronger lock in a world where cyber criminals continually get smarter.
7. Cloud-based Security
Cloud-based security protects the data and applications you store in the cloud using a network of remote servers. It’s your security system for the assets not kept on your property.
These kinds of cyber security solutions are more important than ever since cloud attacks have skyrocketed.
Year-on-year, cloud-conscious attacks have increased by 110%, and cloud environment intrusions have shot up by 75%.

Most small businesses deal with multi-cloud environments these days, making it even harder to keep track. This is where cloud security posture management (CSPM) comes in.
Use cloud security posture management solution to secure multi-cloud environments. CSPM conducts ongoing surveillance and configuration assessments to fortify your cloud infrastructure against ever-evolving threats.
Remember, without cloud security, any data held in the cloud becomes a target for hackers. Whether it’s your website content or web applications, customer data, or intellectual property, you run the risk of theft and misuse.
8. Email Gateway Security
Email gateway security acts as a checkpoint for all incoming and outgoing emails.
It examines the content to make sure nothing harmful gets through. These types of cybersecurity tools block spam, phishing emails, and malware.
The reason these tools are so important is that email is a common way for hackers to trick your workers into providing access to your system.
In fact, 44% of SMBs who experienced a breach last year had their email systems compromised.
Without email security, your business runs the risk of scams and viruses that spread via email with the aim of stealing data or tampering with your accounts.
9. Enterprise Password Management (EPM) /Privileged Access Management (PAM)
Password management is one of the integral cybersecurity solutions for your small business accounts.
But as Scott Schober, President & CEO of Berkeley Varitronics Systems, puts it …
“One of the biggest offenders in small business is that employers and employees do not create and manage passwords properly.”
EPM and PAM help businesses manage and secure passwords and access rights.
Both act as a vault for your secure keys, but they have different focuses.
EPM provides a secure place to manage all passwords. PAM controls access to privileged accounts with high levels of access.
Without these systems, the fallout can be disastrous as hackers gain access to all your private data and digital assets.
For example, last year, due to poor password management, INDRIK SPIDER accessed credentials stored in Azure Key Vault and SharePoint.
In another attack, SCATTERED SPIDER took advantage of the lack of PAM systems and entered a cloud secrets manager, escalating privileges by creating a new admin access key for themselves.
Recognizing this, small businesses are cracking down on password and access security.
59% of SMBs have upgraded their security with two-factor authentication (2FA), while 37% have put access controls in place.
10. Authentication Services/VPN
Authentication services and VPNs are all about secure network access.
They provide a safe way for employees to enter your systems, whether they’re working in the office or remotely.
Well managed services for authentication not only keep unauthorized users out. They also use encryption tools to obscure all data sent over the internet, so it’s safe from prying eyes.
VPNs can be a powerful tool to keep your business data safe, but choosing the wrong provider can cause more headaches than you may have expected.
Make sure that you choose a transparent and open-source VPN if you’re looking for maximum transparency.
Without these services, your network security level is “open to anyone”. If sensitive information is intercepted, hackers can read and understand the data, making it easy for them to use it to their advantage.
With authentication services and VPNs, hackers can’t understand the data even if they get in, as it’s encoded, keeping it hidden and secure.
11. Endpoint Protection
Endpoint protection cybersecurity solutions provide security for each device connected to your network, from laptops to smartphones.
It stops harmful software and hackers from getting into your system through the “endpoints” — the devices your workers use.
These devices can act as inadvertent gateways to your business’s network.
For example, if one of your team members uses a poorly protected laptop at home, a hacker could enter through their device and find their way into your system.
Endpoint security prevents this. It stops viruses, ransomware, and spyware that leak through these devices.
12. Logging and Log Monitoring
Logging and log monitoring act as the business’s security memory. They record everything that occurs on the network, analyzing each log for signs of suspicious activity.
This helps security teams spot problems early and catch signs of hacking, system failures, or misuse of information.
If you choose not to track your logs, you’ll miss the warnings of a cyberattack. This makes it harder to stop them before they do damage.
It also makes it far more challenging to work out what happens after an incident occurs.
13. System Recovery
Obviously, you want to try to stop a security breach before it happens. But even the most robust security systems can sometimes fall victim to a hacker.
System recovery is your Plan B. If a cyberattack occurs, these tools get your systems and data back up and running.
To ensure business continuity, it’s important to have a short Recovery Time Objective (RTO) — the acceptable timeframe for restoring critical systems after an attack.
Robust system recovery tools can significantly reduce RTOs by facilitating faster data recovery and system restoration. This minimizes downtime, lost productivity, and potential revenue and data loss for small businesses.
Without this, recovery could be slow and costly.
This can result in long-term damage to your business’s reputation and bottom line.
How to Choose the Right Cybersecurity Solutions for your SMB
Choosing the right cybersecurity solution is a big deal. It’s like picking the best locks for your doors and windows to keep burglars out.
Here’s how to make sure you get the best protection.
Multi-Layered Defense
Find something that’s got it all.
Look for tools that give you all-in-one protection, like an antivirus with anti-malware, email security, advanced threat detection, and intrusion prevention.
By combining tools, you get a centralized console to control your security, and it’s often more cost-efficient.
Automatic Updates
Your security software should update on its own.
If you have to update manually, you may miss patches and improvements that block out new threats.
Think of it as constantly adding new, more sophisticated locks to your doors to match the new picks the intruders are using.
Easy Management
If a system is simple to use, your team will find it easier to understand.
Look for an easy-to-use interface with intuitive security tools and straightforward analytics that show you exactly what’s going on.
Data Backup & Recovery
Your solution should back up your data automatically.
This makes sure that your digital assets are secure even if your system goes down. It’s a safety net for the worst-case scenario.
Employee Training
Find solutions that offer training to teach your team how to avoid dangers.
It’s not just about having a sophisticated security system. It’s also about making sure your team is vigilant and protecting themselves against scams that require their participation.
Scalability
If you’re planning to expand, pick a system that grows with your business.
As you scale up, you’ll need to add more protection and secure more data sets and digital assets.
It’s better if you can simply upgrade your system rather than having to migrate to a brand-new enterprise tool.
Device Coverage
Consider the coverage your security solutions offer.
It’s no good simply protecting office laptops if lots of remote work is done via mobile devices.
Every device can act as a door into your business, so make sure each one is locked down.
Customer Reviews
Listen to what other customers have to say.
Look for reviews from companies like yours to see if they’re happy with their security.
Customer stories can give you detailed insights into how well solutions work and whether they’re good value for money.
Recap on Cybersecurity Solutions: Secure your SMB at every level
Unfortunately, cybersecurity isn’t as simple as a quick antivirus tool anymore. Cyberattacks are evolving as hackers get smarter every day.
The only way to keep up is to make sure you have multi-layered digital security that addresses your potential vulnerabilities.
Don’t get overwhelmed by the sheer breadth of the cybersecurity space. Consider the priorities for your business and work out which security issues need to be addressed first.
If you’re most worried about identity theft, it’s a good idea to start with anonymous browsing. This hides your digital fingerprint so that hackers can’t see what you’re doing through your browser.
If you’re ready to kick off your hidden browsing journey, try GoLogin antidetect browser on a 7-day free trial.