Every time we visit a website or use internet services, we leave a trace of some data which is used to identify us. One such advanced technique is device fingerprinting, which gathers distinct details regarding your device so that it is able to monitor what you are doing on the internet.
These days, it is easy to delete or block cookies, but evading device fingerprinting is quite difficult as it may not be visible most of the time.
However, what does device fingerprinting mean, how does it work and is it something that should concern you?
What Is Device Fingerprinting?
The method of device fingerprinting is employed for recognizing and tracking users based on their devices’ unique characteristics and configurations. While cookies work by keeping small pieces of information in your device, device fingerprinting collects vast amounts of information that helps it create a unique identifier for every device.
Every time you access a website, information is gathered about your device. Such may include:
- your browser type
- operating system
- fonts installed
- screen resolution
- time zone
- dozens of other device characteristics.
Individually, these details seem irrelevant, but they form a distinct fingerprint of your device among millions.
Device fingerprinting is unique in that it can be done without bothering the user for consent or interaction. Most of the time, this process occurs passively, so that you may not see it while surfing through pages on the internet.
That’s why it is very useful to advertisers, people who work in cybersecurity, as well as those website operators that may wish to monitor users without depending on common methods such as cookies that are susceptible to blocking out or deleting.
Cookies vs. Browser Fingerprint vs. Device Fingerprint
It is very important to distinguish cookies, browser fingerprints and device fingerprints when it comes to online tracking and privacy. Every one of these techniques is distinct in nature and has different effects on the privacy of users.
1. Cookies
When you visit a website, it stores some information on your device in the form of cookies. These files are very useful since they can keep you logged in, remember your preferences as well as follow your activity around the website.
Even though cookies can be seen as plain or simple, they have their own disadvantages with regards to privacy.
Because these cookies are kept in your device, you have the freedom to deny or prevent them through your browser settings. In essence, this makes the cookies non-permanent and easier to handle.
2. Browser Fingerprint
Browser fingerprinting is a method used to gather information about a web user’s browser and its configuration for identification. It takes note of data like browser type, language, version, plug-ins installed, and even HTML5 canvas size (see canvas fingerprinting).
On the other hand, unlike cookies which depend on saving information in your equipment, browser fingerprints make use of a special combination of attributes from your browser.
Although circumventing browser fingerprints may prove more challenging than doing so with cookies, this technique is not entirely independent of the browser and its settings; for example, users can make their fingerprint less unique by using antidetect browsers or turning off some plugins. We’ll mention some details on antidetect use below.
3. Device Fingerprint
Device fingerprinting takes things to another level. It gathers information about your whole device and not just the browser. Here, the method gathers data like the operating system, hardware among other systems’ attributes beside those collected through browser fingerprinting alone.
Combining all these variables results into a unique profile for your device. This approach is not heavily dependent on browsers’ set up and can adapt better to alterations, being an effective way of tracking. It is also more challenging for users to alter or hide these attributes, which raises significant privacy concerns.
What Information Is Collected to Create a Device Fingerprint?
This fingerprint is assembled from various characteristics and configurations, some of which may seem trivial on their own but, when combined, form a profile that’s difficult to duplicate.
Here’s a closer look at the types of information typically collected to create a device fingerprint:
1. Browser and Operating System Details
Information regarding the browser and operating system is among the initial data collected. It includes:
- the browser type (such as Chrome, Firefox) and its version,
- the particular operating system of your device (for example, Windows, macOS, iOS, Android).
The combination of your browser and device operating system can already start to narrow down the pool of possible devices.
2. Screen Resolution and Display Settings
Other display settings such as screen resolution, color depth of your device are recorded too. Due to the fact that these settings differ greatly among devices and are usually altered by users, they can be very helpful in creating a distinct fingerprint.
3. Installed Fonts and Plugins
Device fingerprinting is greatly affected by the list of fonts that you have installed in your device as well as any browser plugins or extensions that you may use. Each user has different fonts and plugins, and when combined with other factors, they can be used to identify individual devices.
4. Hardware Specifications
Another aspect of device fingerprinting is gathering information about the hardware which may include the model of your device, type of CPU, details of GPU and even data concerning your network cards. Such properties increase the uniqueness of the fingerprint of your device.
5. Time Zone and Language Settings
Additional information such as your time zone and preferred language settings can be used to fine tune the fingerprint of your device. Although these options are not very unique alone, they make it possible to create an inclusive profile by combining them with other data.
6. IP Address and Geolocation Data
Even though they may not always be included in the main fingerprinting procedure, the IP address and geolocation data can help in tracking your device’s location and movement over time. This adds another dimension to the profile, particularly useful for tracking and targeting purposes.’
7. Device Metadata
Sometimes, information about your device such as battery status, its touch capabilities and whether your device is plugged in can be gathered. Such data may appear insignificant, but it helps in establishing unique fingerprints across devices which are difficult to replicate.
8. Unique Identifiers
Although not easily accessible due to most devices’ privacy controls, websites can still get device-specific identifiers such as MAC addresses or unique device IDs. Still, when these are acquired, they add a very accurate component to the fingerprint.
How Does Device Fingerprinting Work?
1. Data Collection
As soon as you open a website or access internet services, this is when the whole process kicks off.
A lot of data is taken by these websites or services automatically from your device, even though you may not have done anything or there were no signals for that. Some of the data points that are collected may be:
- Browser Information: Your web browser’s type, version, language, and installed plugins and extensions.
- Operating System Details: Your operating system type and version, together with system settings such as time zone and language preferences.
- Screen Resolution and Display Settings: Your device’s screen resolution, color depth, and other display-related characteristics.
- Installed Fonts and Software: The list of fonts and software installed on your device, which can be unique depending on your preferences and usage.
- Hardware Characteristics: Information about your device’s hardware, such as the CPU type, GPU, available memory, and other components.
- Network Information: Details like your IP address and possibly even more specific network data such as your MAC address, though this is less common due to privacy controls.
2. Data Aggregation
After collecting information, it is combined in a profile that can only belong to an individual device. The procedure includes studying every piece of information and bringing them together so that there is a unique combination which cannot occur in any other device.
For instance, while many people might use the same browser or operating system, the specific combination of browser version, installed fonts, screen resolution, and other details is likely unique to your device.
3. Hashing and Fingerprint Creation
After aggregating the data, the information is often hashed—a process that converts the collected data into a fixed-size string of characters. This hash is what can be referred to as the fingerprint of the device.
Hashing ensures that the fingerprint is concise and easy to compare against other fingerprints while still being unique.
4. Fingerprint Storage and Matching
After creation, the site or service saves the fingerprint in a database. The stored fingerprints are then compared with the new fingerprint of your desktop or mobile device every time you visit the website or follow a link to another site.
In case of finding corresponding results, it identifies your device and enables the tracking of your activity, as well as application of customized preferences or additional safety precautions with respect to the interaction on this particular website.
5. Cross-Site Tracking
The use of device fingerprints is very efficient in monitoring users as they move from one website to another.
It is possible to track a person’s activities on various websites even if they do not log in or allow cookies. The fingerprint does not change and it can be linked with everything on the internet to form a digital profile through machine learning.
6. Adaptation to Changes
One of the strengths of device fingerprinting to identify users – it can change according to your device settings.
It does not matter if you upgrade your browser, add new fonts, or modify screen resolution. In most cases the fingerprinting algorithm will be able to identify your device by analyzing the underlying data that is unchangeable, or by refreshing the stored fingerprint with the current settings.
What is Device Fingerprinting Used For?
The use of device fingerprinting is common in different sectors to help in identification. It can be used for identification, security as well as customization in many sectors. Here’s a look at some of the key uses:
1. Online Tracking and Advertising
Online advertising and tracking is among the primary uses of device fingerprinting. In following users through various sites and noting down what they like doing most, advertisers are able to create profiles that help them know where to best place their products depending on user behaviors.
That’s why user personal data with personal preferences (collected from social media) can be very expensive.
This allows for more precise targeting of ads, often leading to higher conversion rates. Unlike cookies that are easily removed by users, device fingerprinting provides a more persistent method of tracking.
2. Fraud Detection and Prevention
Device fingerprinting is employed by financial institutions, e-commerce platforms and cybersecurity companies in the fraud prevention and detection.
By identifying the unique characteristics of a device, they can spot suspicious activities, such as multiple accounts being accessed from the same device or trying to transact using devices that had been flagged for fraudulent behavior in the past. That’s how social media platforms tell which account to restrict or block.
3. Enhanced Security
Device fingerprinting does more than just prevent fraud; it also adds to user verification.
For example, when someone tries to log in using a device that is not recognized by the system, additional measures of authentication may be demanded such as running a two-factor authentication (2FA) process so as to establish the person’s identity beyond doubt.
4. Personalization of Services
Device fingerprinting is a technique employed by websites and internet based services for customizing user experience.
It enables them to identify your device and customize content, settings, as well as suggestions to fit your needs even if you don’t login or restore your preferred options on every visit. As a result, this may enhance the overall appeal of the site as it will be easier to use.
Risks Associated with Device Fingerprinting
Device fingerprinting has its advantages but it is very risky especially concerning the privacy and freedom of users:
1. Invasion of Privacy
Device fingerprinting poses the greatest risk to privacy. With device fingerprinting, one can be followed online across different websites even without giving the consent or being aware of it.
Companies can therefore gather information on what you do on the internet such as your interests and behaviors. This data may be used for various purposes, and it could also be sold or shared without your consent, most times without you knowing it.
2. Lack of User Control
Cookies can be blocked or deleted by users, unlike device fingerprinting which is difficult to control, identify and track. A majority of users do not know that device fingerprinting exists, and there are not many applications which can be used to stop it from working effectively.
This absence of visibility and authority can make users feel powerless over how their data is collected and used.
3. Potential for Discrimination
The data collected through device fingerprinting can be used to discriminate against certain users.
For example, companies might charge different prices based on your browsing history, location, or device type—a practice known as price discrimination. This can lead to unfair treatment of certain groups of users.
4. Security Vulnerabilities
Device fingerprinting is commonly employed to enhance security, however, it also has its own drawbacks.
In case malicious users get hold of your device’s fingerprint, they can mimic your device and gain unauthorized entry into your accounts or systems that are secured by fingerprint biometrics.
Legal Regulations Around Device Fingerprinting
Given the privacy concerns associated with device fingerprinting, it’s subject to increasing scrutiny and regulation around the world. Here’s an overview of the current legal landscape:
1. General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) of the European Union is very clear about the manner in which an individual’s information, especially on device fingerprinting, is to be gathered, handled and kept. Under the GDPR, any information that can be used to identify an individual, directly or indirectly, is considered personal data.
As such, device fingerprinting data is considered to be within the scope of the GDPR, and businesses have to seek for explicit permission from customers before gathering such information.
2. California Consumer Privacy Act (CCPA)
In the United States, the CCPA provides similar protections for residents of California. The CCPA grants consumers the right to know what personal information is being collected about them, the right to request that this information be deleted, and the right to opt out of the sale of their personal data. Companies that use device fingerprinting must disclose this practice to consumers and provide them with the ability to opt out.
3. Children’s Online Privacy Protection Act (COPPA)
The collection, utilization and dissemination of information gathered from children under 13 years is regulated by a federal law called COPPA in the US. Websites and other online platforms are required by COPPA to get parental permission first before they collect, use, or share any information about children.
4. Other Global Regulations
Device fingerprinting is being affected by the privacy legislations that are emerging or being updated not only in the European Union and the United States but also in other regions.
Some of these laws include:
- The General Data Protection Law (LGPD) of Brazil
- The Personal Information Protection and Electronic Documents Act (PIPEDA) of Canada
These contain some clauses on controlling the gathering and utilization of personal information, posing possible challenges on the applicable nature of device fingerprinting.
The Importance of Device Fingerprinting
To begin with, this is an effective weapon against fraud for companies since it can tell if the online transactions or account logins are from trusted parties.
This added layer of security helps protect users and companies from malicious activities such as account takeovers and identity theft. In addition, device fingerprinting allows companies to give customized experiences by adjusting the information and ads to fit each user, all this without having to use invasive cookies.
On the other side, it creates invasions into the users’ freedom and data protection rights.
It is important to see a balance between such factors so that the technology can be applied in a responsible and moral manner for the good of all parties involved, including customers and companies.
Can Users Block Device Fingerprinting?
Device fingerprinting is a strong tracking tool but there are ways through which users can minimize its impact and improve their digital privacy. It should be noted that preventing all forms of device fingerprinting may be difficult because of its complexity.
Some of the tips that can be used by the user to enhance their privacy are:
Adjust Browser Settings
Many modern browsers offer privacy settings that can help mitigate device fingerprinting. Users can:
- Disable JavaScript: Since JavaScript is often used to collect various device details, disabling it can reduce data collection, though this may impact website functionality.
- Block Third-Party Cookies: Even though it does not directly prevent fingerprinting, it is possible to reduce some tracking techniques employed alongside fingerprinting by blocking third-party cookies.
- Clear Browsing Data Regularly: Regularly deleting cookies with special cookie tools, cache as well as other browsing data may reduce monitoring but does not deal with fingerprinting in particular.
Limit Online Activity
Reducing the amount of personal information you share online can help mitigate the effectiveness of device fingerprinting.
For instance, using disposable email addresses or avoiding the submission of personal information like phone numbers and addresses can reduce the amount of identifiable data that is available to trackers.
Nonetheless, this strategy may limit your interaction with various online services and affect the overall user experience, especially social media.
Use a Browser Fingerprint Checker
Tools like iphey.com offer a reliable browser fingerprint checker that allows you to see exactly what data points websites are collecting about you. By using this service, you can get a detailed report of your browser’s fingerprint, including information such as your browser type, version, operating system, screen resolution, and more.
- How It Helps: Knowing what data is exposed helps you understand your vulnerability to tracking and allows you to take specific actions to protect yourself and avoid identity theft.
Get An Antidetect Browser
There are new generation privacy browsers, designed to completely stop sharing your information during your online sessions, called antidetect browsers. They provide multiple browser profiles, each with a clean and real new device fingerprint.
Most of these are commercial because they’re used in digital marketing a lot, however most have free plans for personal use. Antidetects also provide good proxy IP management features, which in total enables you to reach complete anonymity.
We’ll show an example of an antidetect below.
What is GoLogin Antidetect Browser?
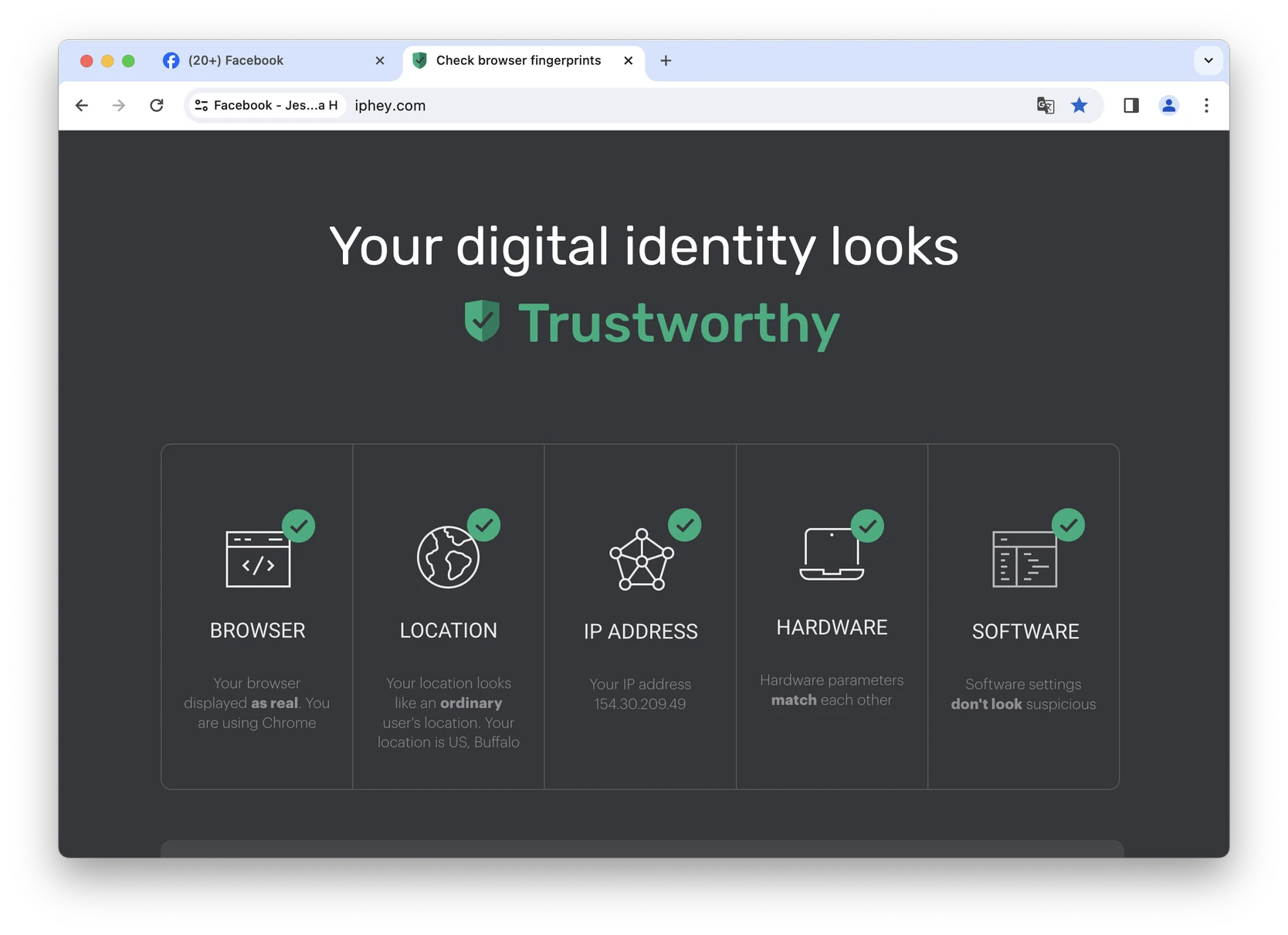
GoLogin is one of the top tools on the market that helps protect your privacy by managing your complete device fingerprint + IP address.
With Gologin’s antidetect technology, you can surf the net with total anonymity – there is a close to zero chance of being traced on even most advanced websites, including even social and crypto platforms with extreme tracking.
In contrast to VPN (virtual private network) tools that encrypt your real parameters causing suspicion, GoLogin provides you with a new device fingerprint and clean IP address.
It’s specifically designed to enhance your privacy by preventing tracking and monitoring in the first place, not by masking or selling your information.
How GoLogin Is Used For Marketing Businesses
GoLogin and other antidetects are changing the game for many digital businesses, allowing for comfortable and safe social media use on a business scale.
Here’s how it’s used for Facebook and other social media:
If you run a business that needs anonymous surfing to protect your data from excessive device fingerprinting, website blocks and restrictions, GoLogin offers a reliable antidetect browser solution.
It will provide completely anonymous browsing that’s also helpful for marketing needs such as running multiple accounts with no restrictions.
Named Easiest to use antidetect browser according to G2 reviews, GoLogin is an essential tool for comprehensive protection against device fingerprinting, identity-based cyber attacks and account loss.
Recap on What Is Device Fingerprinting
- A device fingerprint refers to the various personal data that is collected about your device while using the internet. Fingerprinting is done without notice.
- Device fingerprinting has its positive use cases (like finance systems safety), but it’s often used to track users without consent for commercial reasons.
- There are several ways to manage and minimize tracking, including limiting your online activity, managing cookies and using antidetect browsers.
- Tools like GoLogin antidetect browser offer real anonymity and protection against device fingerprinting, compared to incognito mode, VPNs and proxies and common privacy browsers.
GoLogin offers a free plan for personal use which is best for anonymity – try it out today!