The amount of digital information in the world doubles every two years. The number of searches for “how to hide your identity” is also increasing every year. For the most part, this is the personal data of users. We use smartphones, computers, tablets, IoT devices – they all collect usage information. We pay for purchases at online banks, book tickets, and communicate with friends online. Our kids do their homework online. On the Internet, we work, communicate, and even look for a soul mate. The Internet space is changing at a breakneck pace, and data privacy problems are getting worse.

How to hide your identity?
Information is money. It is the main reason why your data is at risk. Advertisers are hunting your browser search history – they can significantly benefit from this information. Let’s say you enter “apartment for rent” or “buy an apartment” in the search bar. After seeing your search history, the advertiser will know that you are planning to move soon. It is an excuse to show you advertisements for cargo taxis, furniture, building materials stores, and insurance companies.
It is perfectly legal. However, fraudsters can also make money on your data. Credit card data is openly traded on the dark web. So it is a great success for a cybercriminal to access an airline’s booking system or an online store’s customer base. Attackers can use any information that you post on the web, which is why it is essential to keep your personal data safe. Let’s look at why online privacy is so important and how you can protect your data.
Incognito mode
One of the ways to protect your personal data online is to use incognito mode. Almost all modern browsers have an incognito mode. But not everyone understands how much it protects online privacy. Let’s take a closer look at what incognito mode can and can’t hide.
Many people care about online privacy: no one wants personal information to fall into the wrong hands. There are several ways of protection, and one of them is the “incognito” mode. Apple first introduced this feature in the Safari browser in 2005. Since then, between 2008 and 2010, other popular browsers have taken the initiative, including Google Chrome, Internet Explorer (now Edge), Mozilla Firefox, and Opera.
What incognito mode allows you to hide
To not reveal important information on the Internet, you should clearly understand what exactly a browser operating in “incognito” can hide. Incognito mode does not store this data.
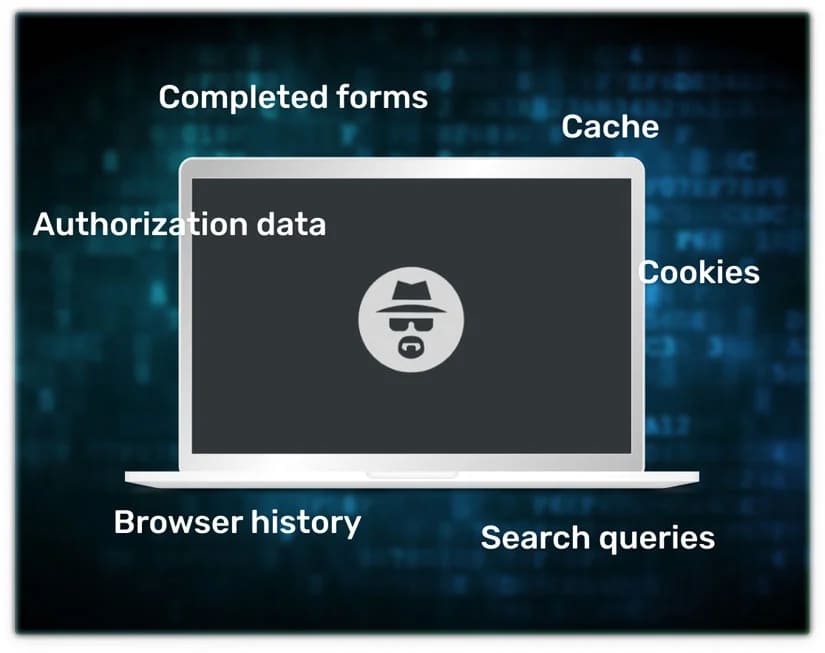
What information will incognito mode not hide?
This mode helps you hide information only from colleagues and family (from local users). However, your views can be seen by ISPs, Wi-Fi owners, websites, and local network administrators. It is a good tool to hide your identity in real life. But is it anonymity? We doubt it. Firefox and Google Chrome warn about this immediately.
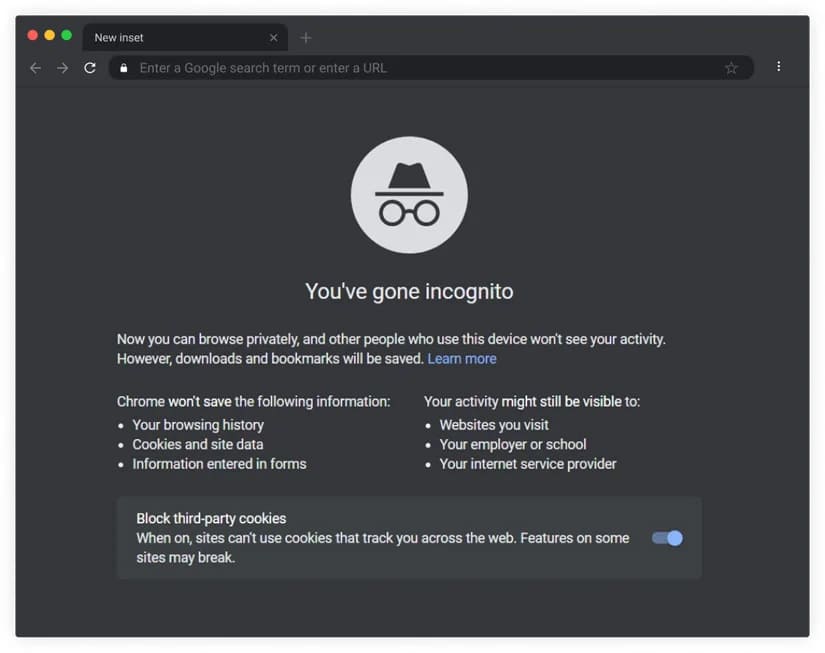
Even if you use incognito mode, providers will see all your visits. They provide you with an IP-address and can relate it to the owner of the computer.
At work, your walks on the Internet can be tracked by local system administrators. Often, companies specifically track visits to specific sites (social networks, instant messengers, and so on) so that employees do not waste time. Remember, incognito mode is useless here. Special software allows you to track which employee quickly, when, for how long, and what resource.
Site owners also receive information about visits: IP-address and some other information, such as browser version, type of device used, and the like. With a strong desire, websites can still track your identity on Instagram, Youtube, Gmail, Facebook, Amazon etc. Sites use this information to display relevant contextual ads. They can also identify the user due to the digital fingerprint left by him – information about IP addresses, browsers used, devices, and pages visited.
How to launch a window in incognito mode
Incognito mode is launched in just a few clicks. Let’s look at the example of the most popular browsers. If you use Google Chrome, click on the icon with three dots in the upper right corner and select the line “New incognito window”.
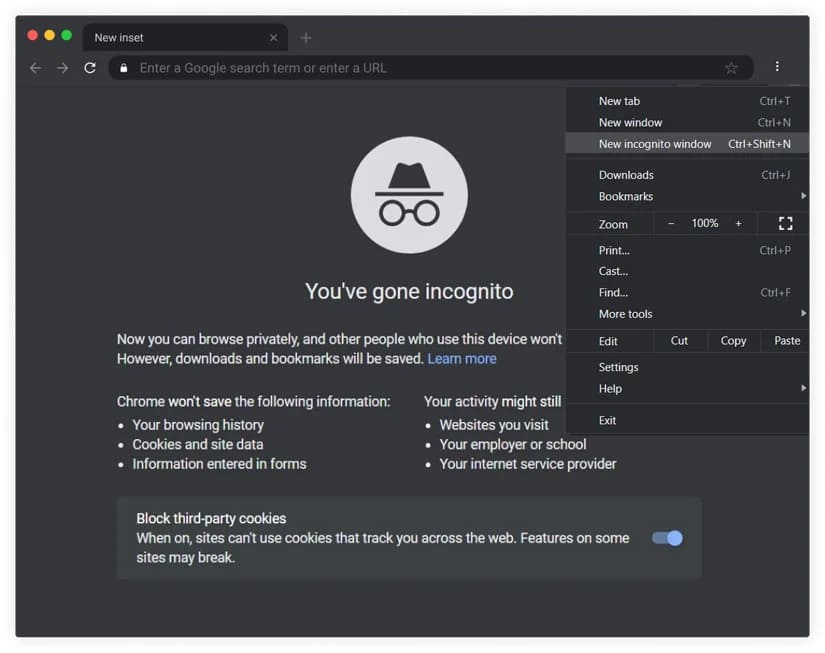
An alternative way is to press the key combination Ctrl + Shift + N. Also, you can use this combination in Opera and Yandex Browser. In Mozilla Firefox, you should press Ctrl + Shift + P.
But remember that incognito mode will not help you completely cover your tracks. This feature is more suitable for hiding searches and history from your family or small work team. Incognito mode is not capable of completely hiding information about what you were doing on the computer.
Tor Browser
Want to know how to hide your identity online? Tor is a technology that allows you to hide a person’s identity on the Internet with some success. Tor was originally a US military project, then it was opened to sponsors and is now called the Tor Project. This network’s main idea is to provide anonymity and security in a network where most of the participants do not trust each other. This network’s essence is that data passes through several computers, is encrypted, their IP address changes, and you get a secure data transmission channel.
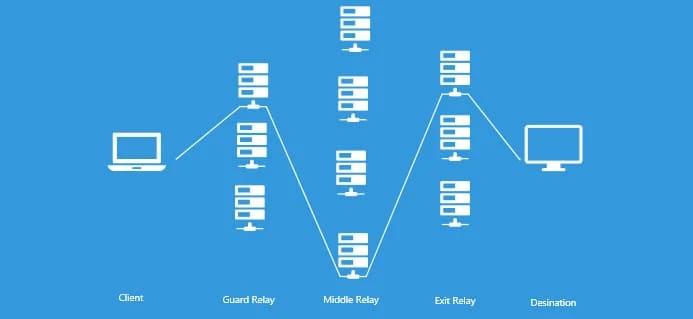
The principle of Tor is the same as in films about hackers: it takes turns connecting to the site or service you need through several servers. Usually, three nodes participate in the chain: guard, middle, and exit relay. Before a request or data goes to the network, a special program on the user’s computer encrypts it so that each server can only decrypt its part.
Usually, to surf the Internet safely, people use Tor Browser, the official browser from this network’s creators. It already contains all the settings that are needed to connect to the network. Initially, you had to have technical skills to connect to the Tor network. But over time, this procedure has become more comfortable. Now, everyone can download the browser to their computer and launch it with two clicks.
However, we recommend downloading it from the official website or trusted sources because many cybercriminals add viruses and Trojans to the archive. It’s also a good idea to check the file after downloading.
To install the browser, open the downloaded file, select a language, and click install.
It is usually not a problem. But once launched, you will have to connect to the Tor network with a single click. Welcome to the onion network!
However, the Tor browser has its own rather serious drawbacks. Check them out before using:
- Not all of your data is safe. If you use plugins and add-ons, remember that they send your data to the developers. You will not be able to maintain your anonymity.
- The more nodes your connection has, the slower the page loading speed, so your browsing will be much slower than usual.
- Tor is still not completely anonymous. The main problem is the Tor exit nodes. Because of them, others can monitor any unencrypted communication protocols like SMTP, FTP, HTTP. It includes cookies, logins, and passwords, uploaded and downloaded files.
Temp mail
Have you ever thought about the fact that by sending an email, you reveal your identity? And it is! The point is that your actual IP address is stored on mail servers. Therefore, if a government or other competent authority makes a request, Google and other companies will issue your real IP address. Also, don’t forget about data leaks that occur from time to time. And with this data, other people can find your actual location and possibly your real identity!
Therefore, we recommend using temporary mail. Temporary email is a service that allows you to use temporary email for a specified period. Usually, people get one or two registration confirmation emails and leave the site, and their temporary mail is deleted. But you can find services that provide addresses for several days.
It is not difficult to get such a service. You need to find it on the website and generate new mail. To delete all data about it, close the tab!
Anonymous payment systems
Some people using e-commerce don’t want anyone to look up and learn more about them. They are looking for opportunities to conduct accounting anonymously. Still, almost all popular payment systems now require verification and openly work with law enforcement agencies.
There are a lot of anonymous payment systems. If you want to manage your electronic accounts with complete anonymity, it is better to use cryptocurrencies. They do not have data centers. Therefore, no one will be able to track your financial transaction.

How to pay anonymously?
- The most popular cryptocurrency is Bitcoin, and you need to create your crypto wallet. It’s like your debit card.
- After creating your wallet, buy cryptocurrency from one of the famous exchanges. Popularity most often shows the trust of other users in the system.
- After buying a cryptocurrency, you can quickly transfer it and pay for services. Every year more and more companies accept payment in bitcoins.
We will not recommend specific services in this article. Use the most popular ones.
VPN
VPN is a service that allows you to protect private data when using the Internet. Connecting to such a network occurs over your regular internet connection. It means you must have a working internet connection to connect to a VPN. The main difference between the VPN and the standard connection is encryption. All data transmitted over a VPN is encrypted, another easy way to become anonymous and hide your identity. Unfortunately, not 100%.
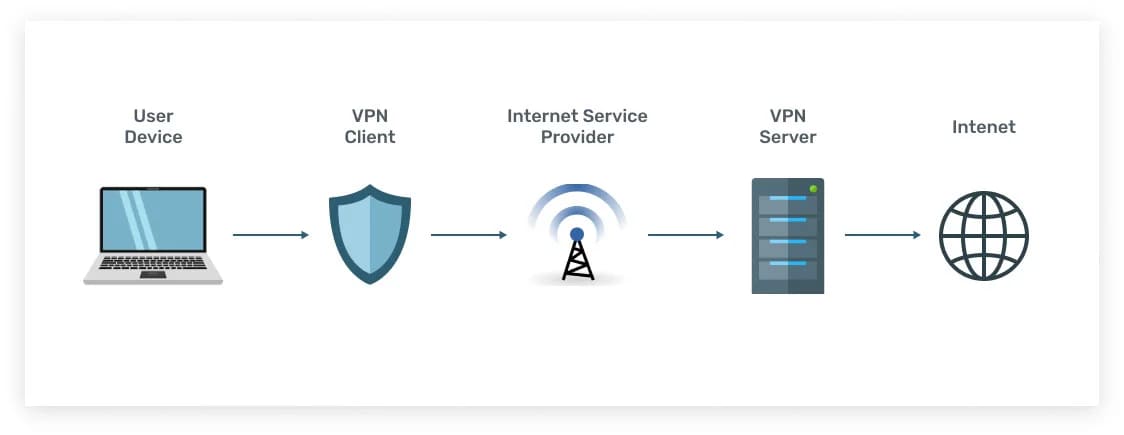
If you work at a computer and want to visit a blocked site using a browser, then you can either install a special program on your PC (VPN client) or add a browser extension. But there are several important disadvantages in this technology:
- Low Internet speed. Additional encryption takes time. Also, traffic often travels a greater distance, which is associated with the remoteness of the VPN server’s location.
- A periodic sudden release of traffic to the public network. You may often not notice disconnected connections and data leakage, and VPN connections may not be restored automatically, which is inconvenient.
- In practice, DNS queries are often processed by the public network’s DNS servers (not the virtual, secure one). In case of their incorrect answer, you can get a fake address of the requested domain. So, unsuspecting users can be redirected, for example, to the sites of fraudulent online banks. Also, using DNS servers, you can determine the approximate geolocation and Internet provider of the user.
- Various legal aspects are also present. First, there are differences in the legislation of different states. VPN clients and VPN servers are often located in other countries. Also, traffic can pass through a third country in transit. Thus, it is possible to save a copy of the transmitted data for further decryption.
Proxy
A proxy server is often called an intermediary because it performs exactly this function and acts as it between the user and the final server. In this case, the presence of an intermediary mayor, in some cases, does not know the party. This method allows you to indirectly send requests to other servers and receive responses from them.
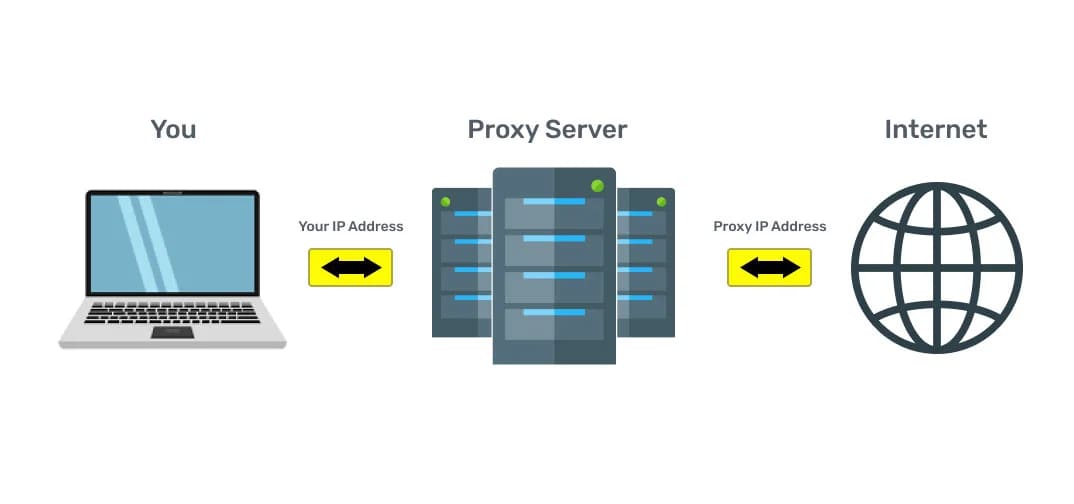
A web proxy allows you to browse the web anonymously as data passes through multiple servers located in different parts of the world. It makes it much more difficult for an attacker to trace your IP.
A secure proxy server acts as a tunnel between your computer and the websites you visit. As long as you use a proxy connection, you get the following benefits: anonymity, privacy, and almost complete freedom.
Connecting through a proxy server only allows you to hide your IP address. But not encrypt the transmitted Internet traffic, so the ISP can still see what you are doing on the Internet.
Proxy servers are only suitable when you need to mask your location. For example, adapt to a country for which there are big discounts in some online stores. Sites track over 100 parameters that can reveal your identity. If you need more anonymity and data protection, it is better to use the GoLogin antidetect browser
Antidetect browser GoLogin
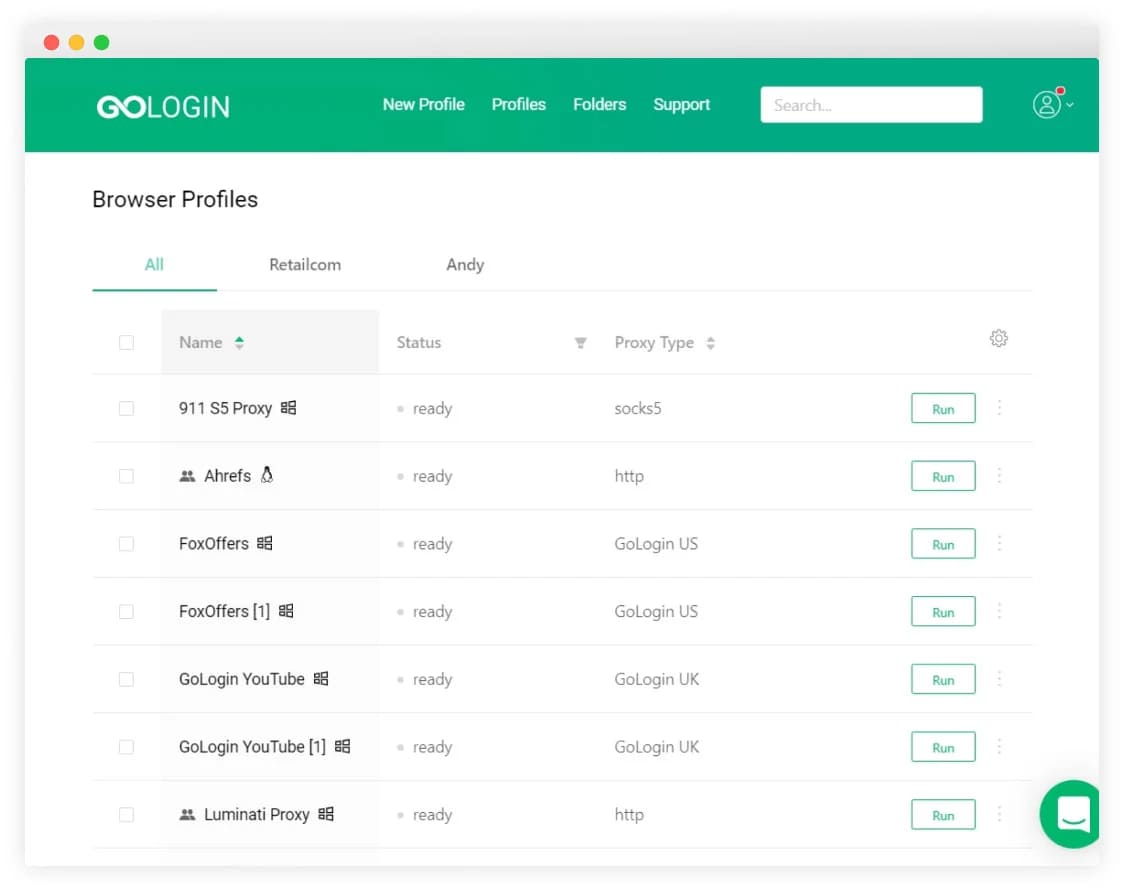
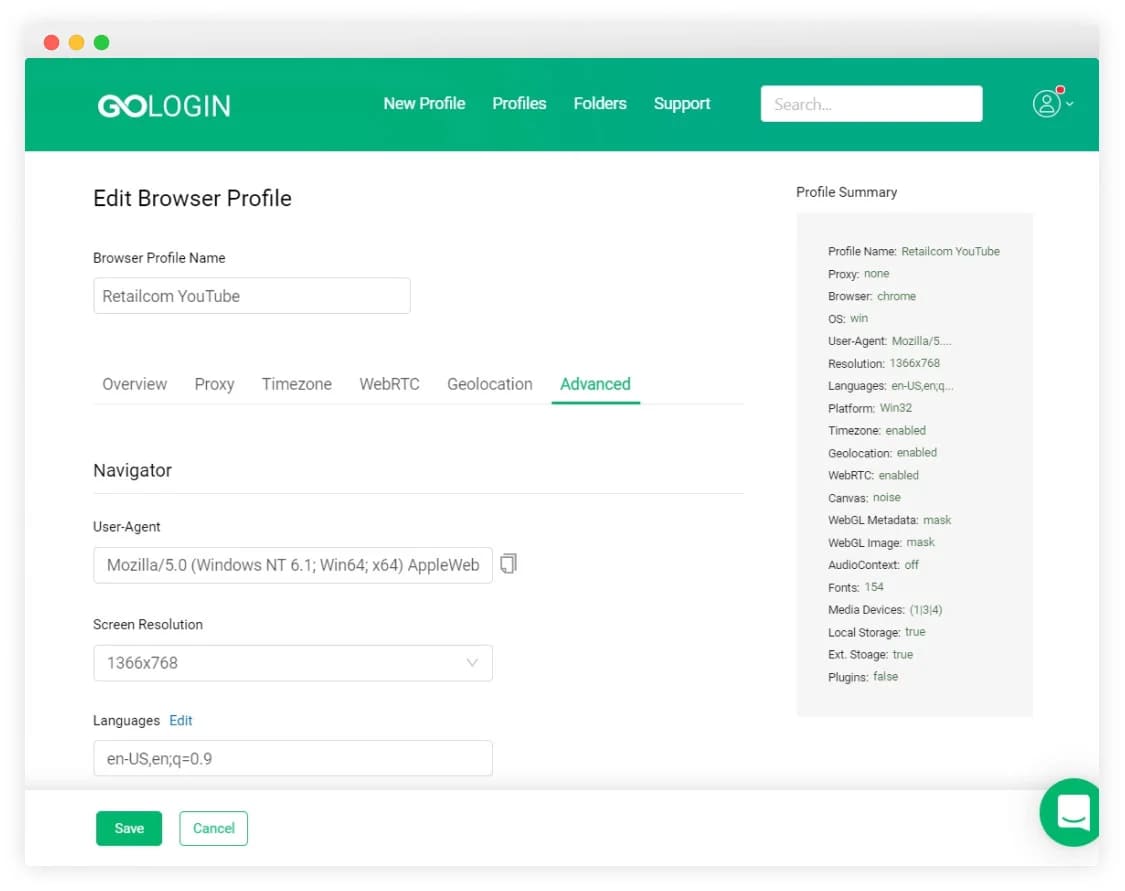
antidetect browser are programs that replace browser fingerprints, uniquely work on the Internet and allow you to work simultaneously with multiple advertising or social accounts. Thanks to antidetect browser like GoLogin, you can replace all your connection parameters. Assign the parameters that sites should see and hide those that you want to keep private.
- Screen Resolution
- Time zone
- Color Depth
- CPU class
- Platform
- Installed fonts
- Plugins
- Is Adblock set or not
- Pixel ratio
- Does the user use the Canvas Blocker
antidetect browser users like the convenience because it is as convenient as your regular browser because it is developed based on Chromium. The speed of work is as high as without using anonymity tools. GoLogin provides free proxies for those who only need anonymity. For multi-account users, it is better to work with their proxies or purchased from providers. If the proxy is of good quality, then you can guarantee yourself 100% anonymity. A free trial period is also available, so you can be convinced of this tool’s effectiveness and choose the plan that suits your needs. There is both a free plan with one profile to use and with more than 1000 profiles. Everyone will gain their anonymity together with GoLogin.


